API Gateway ¶
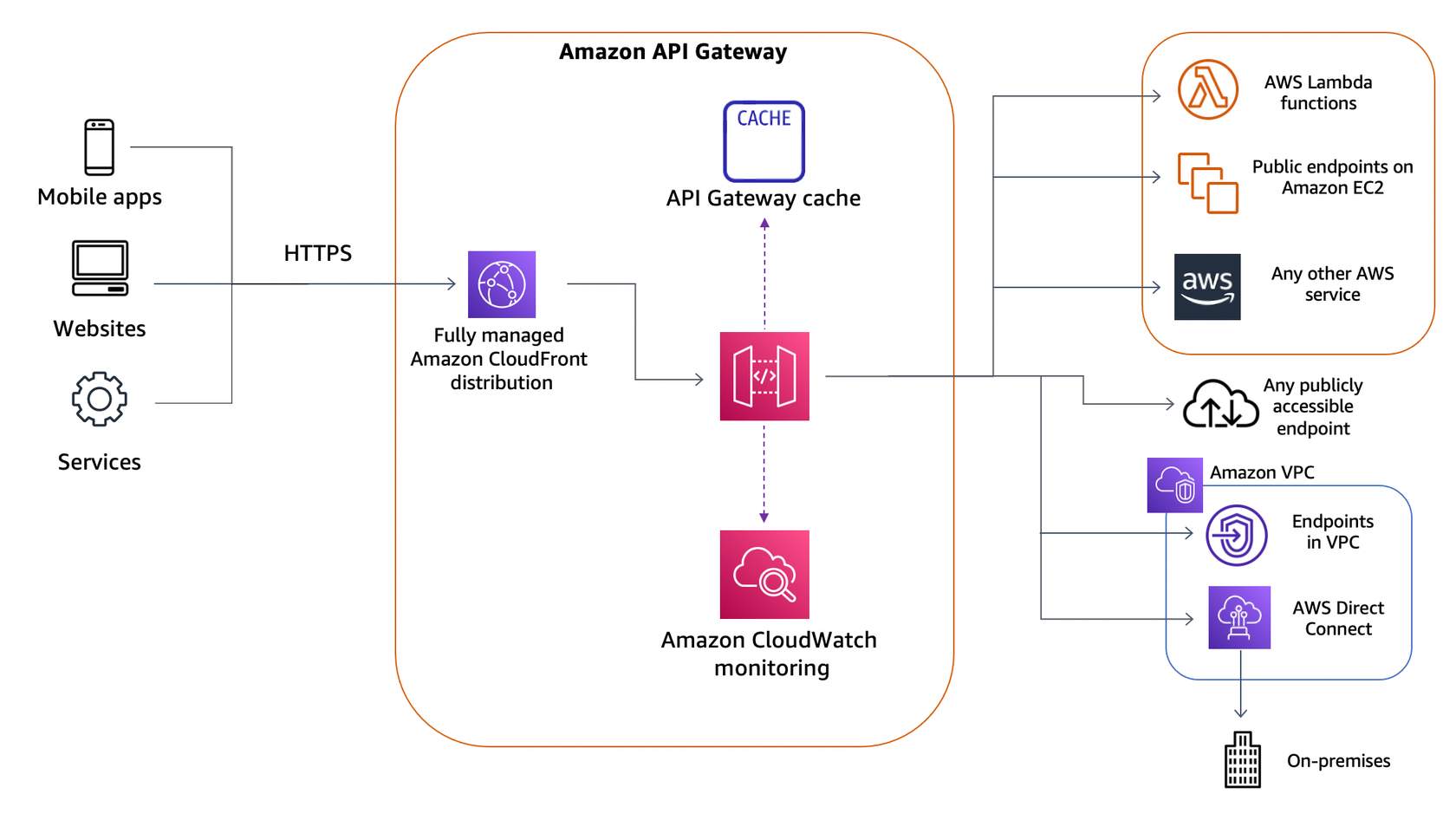
Amazon API Gateway is an AWS service for creating, publishing, maintaining, monitoring, and securing REST, HTTP, and WebSocket APIs at any scale. This includes handling traffic management, Cross Origin Resource Sharing (CORS) support, authorization and access control, throttling, monitoring, and API version management.
API Gateway creates RESTful APIs that:
- Are HTTP-based.
- Enable
statelessclient-server communication. - Implement standard HTTP methods such as GET, POST, PUT, PATCH, and DELETE.
Want to have full-duplex communication: there is a support for web-sockets too?
API Gateway creates WebSocket APIs that:
- Adhere to the WebSocket protocol, which enables stateful, full-duplex communication between client and server.
- Route incoming messages based on message content.
WebSocket APIs are often used in real-time applications such as chat applications, collaboration platforms, multiplayer games, and financial trading platforms.
Features 📋¶
Version 🧮¶
With API Gateway, you can run multiple versions of the same API simultaneously so that you can quickly iterate, test, and release new versions. You can make changes to your API and host multiple versions of it for different users also.
Transform data 📊¶
With API Gateway, you can also transform and validate both incoming and outgoing requests. With this feature, you can use API Gateway as a fully managed environment for transforming requests as they come into your API before they are passed to your backend.
Reduced Latency 🕰️¶
API Gateway provides end users with the lowest possible latency for API requests and responses by taking advantage of the Amazon CloudFront global network of edge locations.
API Throtlling 🪣¶
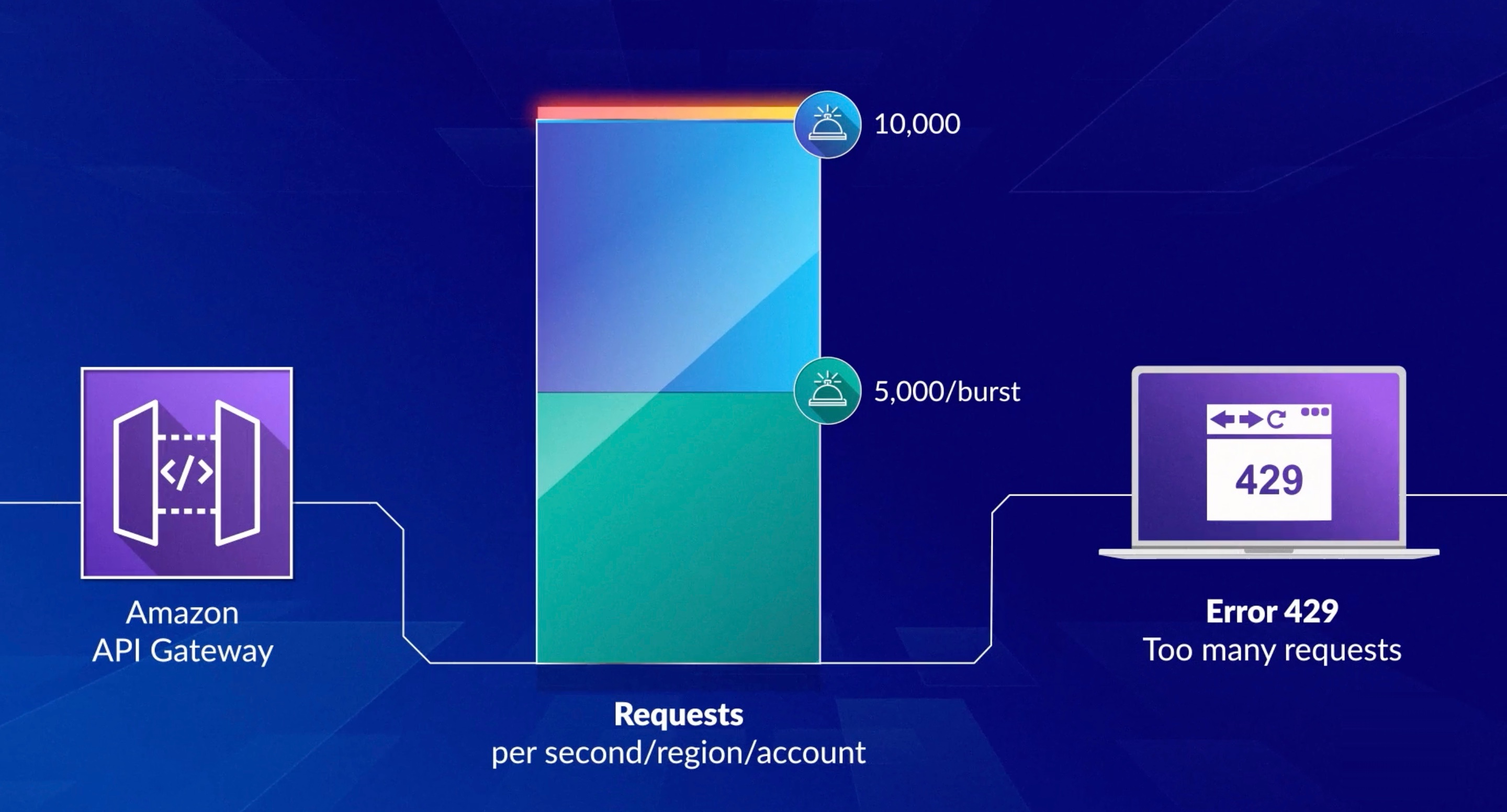
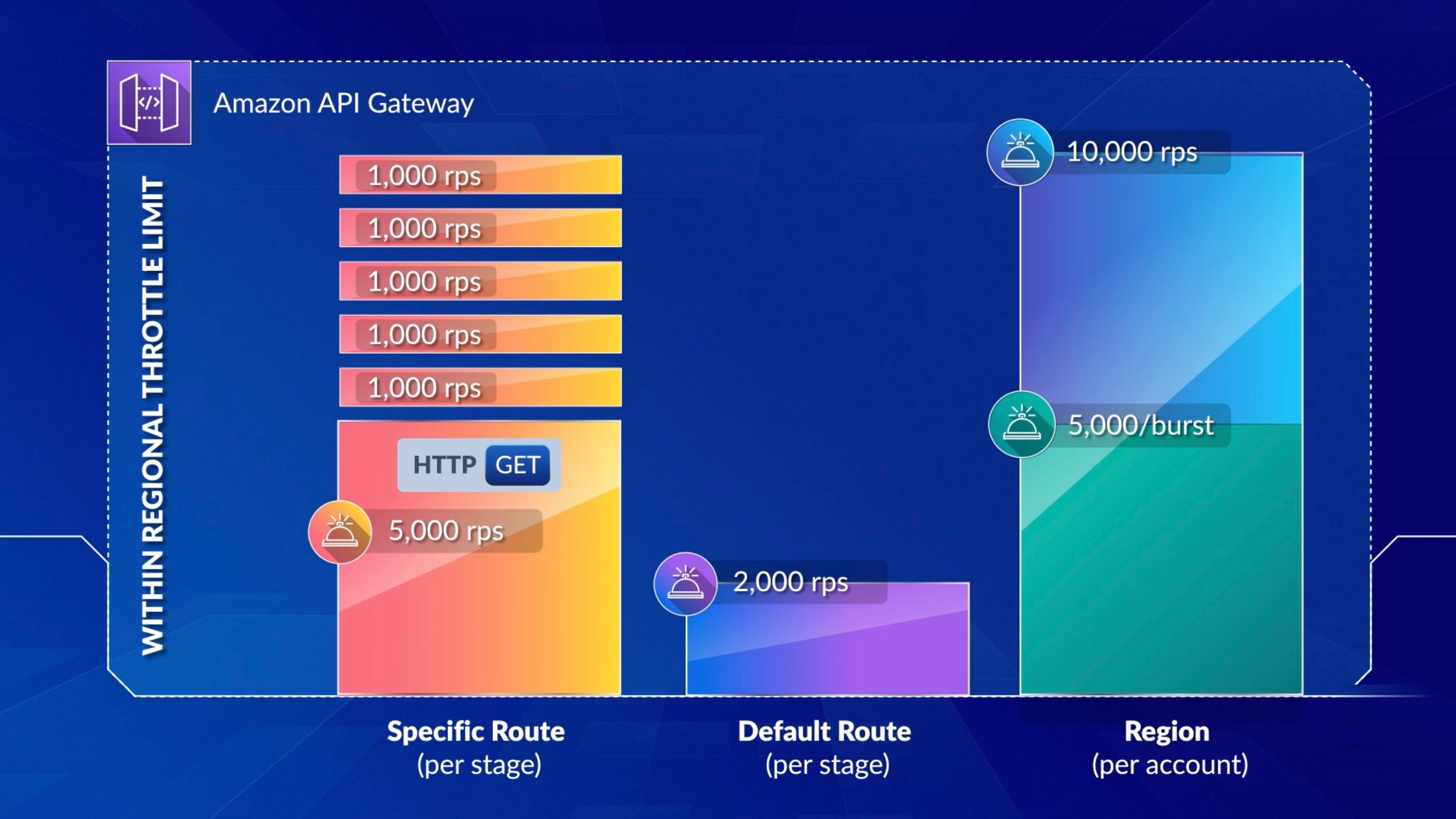
You can configure throttling and quotas for your APIs to help protect them from being overwhelmed by too many requests. Both throttles and quotas are applied on a best-effort basis and should be thought of as targets rather than guaranteed request ceilings.
API Gateway throttles requests to your API using the token bucket algorithm, where a token counts for a request. Specifically, API Gateway examines the rate and a burst of request submissions against all APIs in your account, per Region.
When request submissions exceed the steady-state request rate and burst limits, API Gateway begins to throttle requests. Clients may receive 429 Too Many Requests error responses at this point. Upon catching such exceptions, the client can resubmit the failed requests in a way that is rate limiting.
Info
In a usage plan, you can set a per-method throttling target for all methods at the API or stage level. You can specify a throttling rate, which is the rate, in requests per second, that tokens are added to the token bucket. You can also specify a throttling burst, which is the capacity of the token bucket.
Custom Lambda authorizer 🎫¶
TLDR
A Lambda authorizer (formerly known as a custom authorizer) is an API Gateway feature that uses a Lambda function to control access to your API.
A Lambda authorizer is useful if you want to implement a custom authorization scheme that uses a bearer token authentication strategy such as OAuth or SAML, or that uses request parameters to determine the caller's identity.
When a client makes a request to one of your API's methods, API Gateway calls your Lambda authorizer, which takes the caller's identity as input and returns an IAM policy as output.
Types of Lambda authorizers¶
Info
There are two types of Lambda authorizers:
-
A token-based Lambda authorizer (also called a TOKEN authorizer) receives the caller's identity in a bearer token, such as a JSON Web Token (JWT) or an OAuth token. For an example application, see Open Banking Brazil - Authorization Samples on GitHub.
-
A request parameter-based Lambda authorizer (also called a REQUEST authorizer) receives the caller's identity in a combination of headers, query string parameters, stageVariables, and $context variables.
For WebSocket APIs, only request parameter-based authorizers are supported.
Using custom authorizer
It is possible to use an AWS Lambda function from an AWS account that is different from the one in which you created your API. For more information,
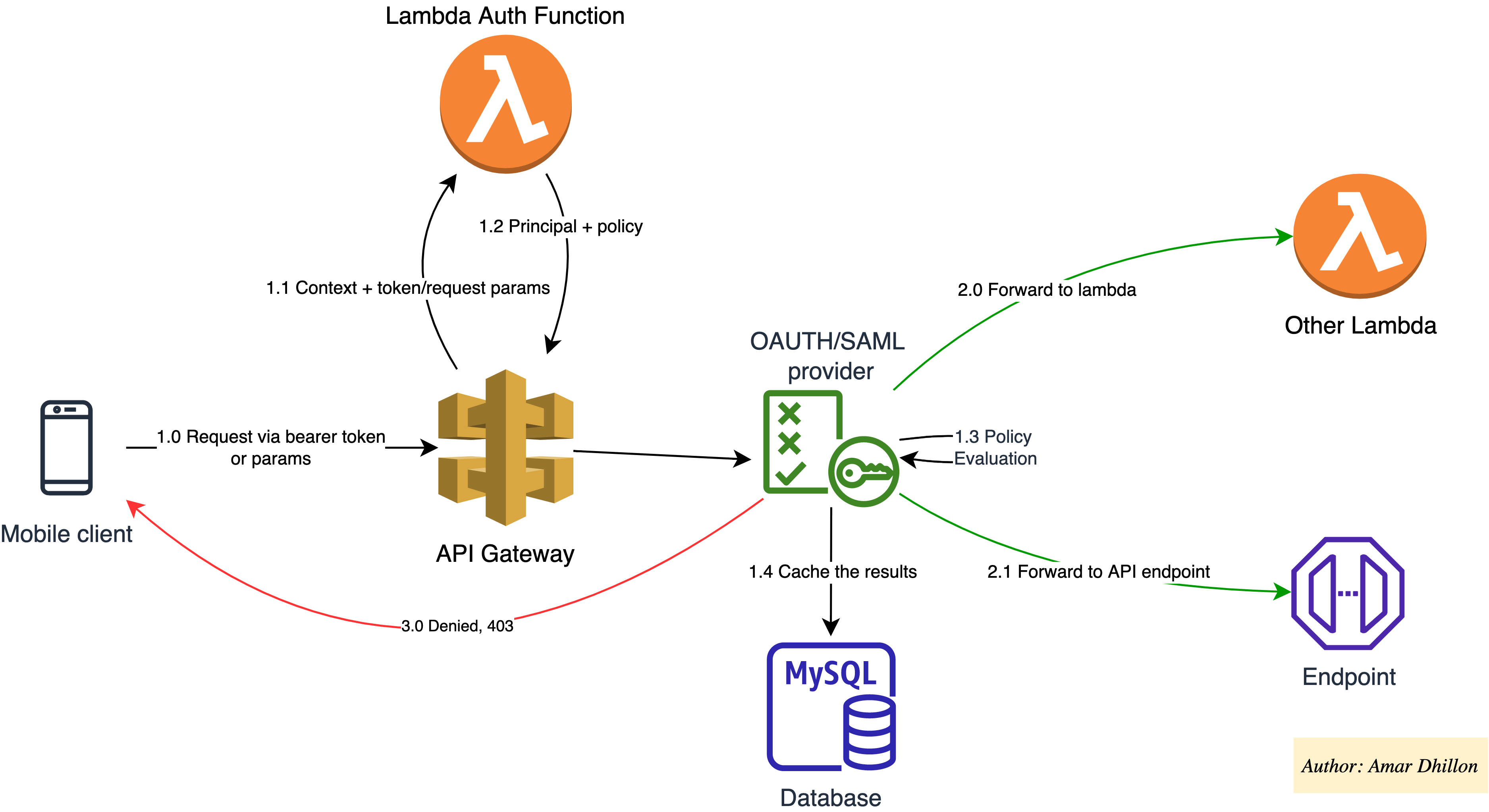
Authorization workflow ⏳¶
- The client calls a method on an API Gateway API method, passing a bearer token or request parameters.
What is Bearer token?
Bearer authentication (also called token authentication) is an HTTP authentication scheme that involves security tokens called bearer tokens. The name “Bearer authentication” can be understood as “give access to the bearer of this token.” The bearer token is a cryptic string, usually generated by the server in response to a login request. The client must send this token in the Authorization header when making requests to protected resources
API Gatewaychecks whether aLambda authorizeris configured for the method. If it is, API Gateway calls the Lambda function.-
The Lambda function authenticates the caller by means such as the following:
- Calling out to an
OAuth providerto get an OAuth access token - Calling out to a
SAML providerto get a SAML assertion. - Generating an
IAM policybased on the request parameter values. - Retrieving credentials from a database.
- Calling out to an
-
If the call succeeds, the
Lambda functiongrants access by returning an output object containing at least anIAM policyand aprincipal identifier. -
API Gateway evaluates the policy.
- If access is denied, API Gateway returns a suitable HTTP status code, such as
403 ACCESS_DENIED. - If access is allowed, API Gateway executes the method. If caching is enabled in the authorizer settings, API Gateway also caches the policy so that the Lambda authorizer function doesn't need to be invoked again.
- If access is denied, API Gateway returns a suitable HTTP status code, such as
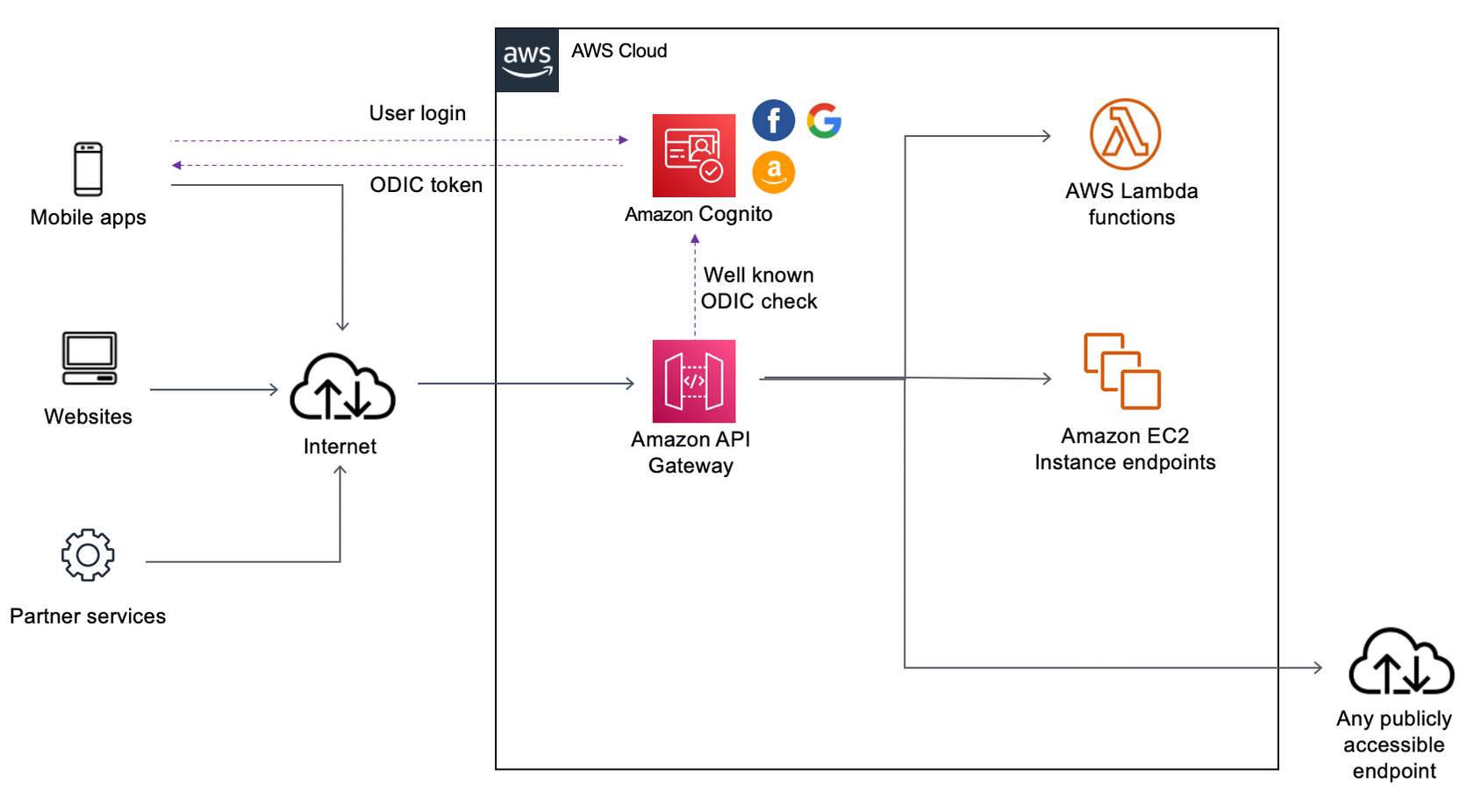
Auth using Cognito 🚨¶
URI 🔗¶
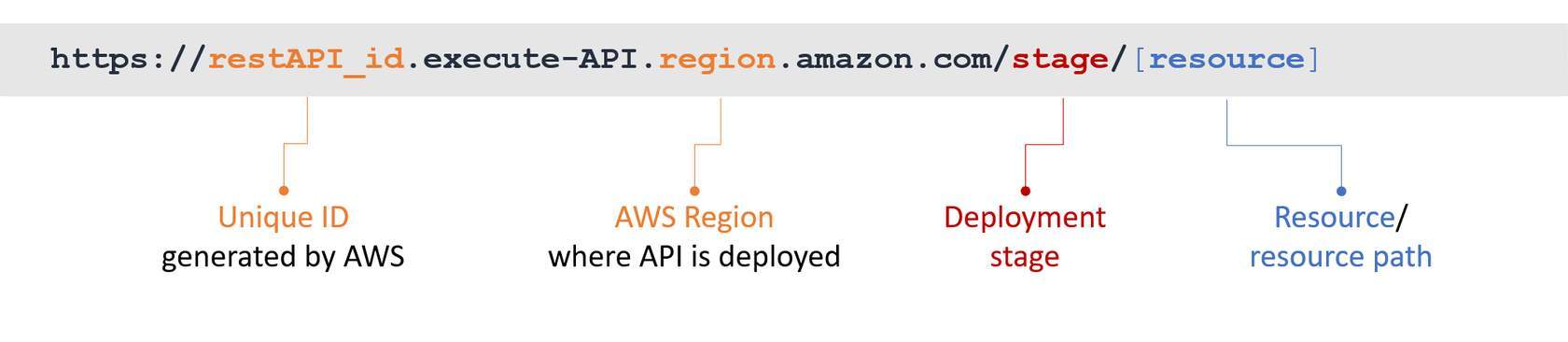
All of the APIs you create with API Gateway will follow the same pattern as you see in the invoke URL above, reflecting the ID of the API and the Region in which you created it, followed by a stage, and then the resource and resource path you want to expose.
Endpoint Types¶
An API endpoint type refers to the hostname of the API. The API endpoint type can be of 3 types depending on where the majority of your API traffic originates from.
- Edge-optimized
- Regional
- Private
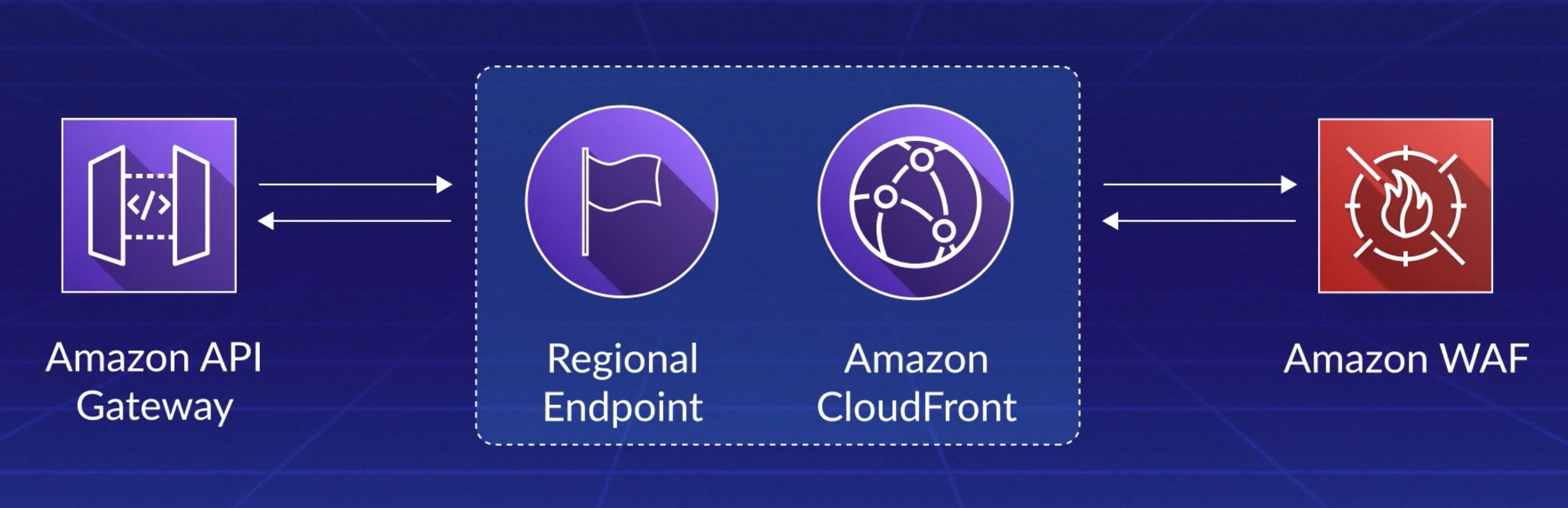
Edge Optimized ⇱¶

An edge-optimized API endpoint typically routes requests to the nearest CloudFront Point of Presence (POP), which could help in cases where your clients are geographically distributed.
This is the default endpoint type for API Gateway REST APIs.
How to prevent DDOS attack?
AWS WAF is a web application firewall that helps protect web applications and APIs from attacks. It enables you to configure a set of rules called a web access control list (web ACL) that allow, block, or count web requests based on customizable web security rules and conditions that you define. For more information, see How AWS WAF Works.
You can use AWS WAF to protect your API Gateway REST API from common web exploits, such as SQL injection and cross-site scripting (XSS) attacks. These could affect API availability and performance, compromise security, or consume excessive resources. For example, you can create rules to allow or block requests from specified IP address ranges, requests from CIDR blocks, requests that originate from a specific country or region, requests that contain malicious SQL code, or requests that contain malicious script.
Regional 🌏¶
A Regional API endpoint is intended for clients in the same region.
Example
When a client running on an EC2 instance calls an API in the same region, or when an API is intended to serve a small number of clients with high demands, a Regional API reduces connection overhead.
Private 🔐¶
A private API endpoint is an API endpoint that can only be accessed from your Amazon VPC using an interface VPC endpoint, which is an endpoint network interface (ENI) that you create in your VPC.
Integrations 🌐¶
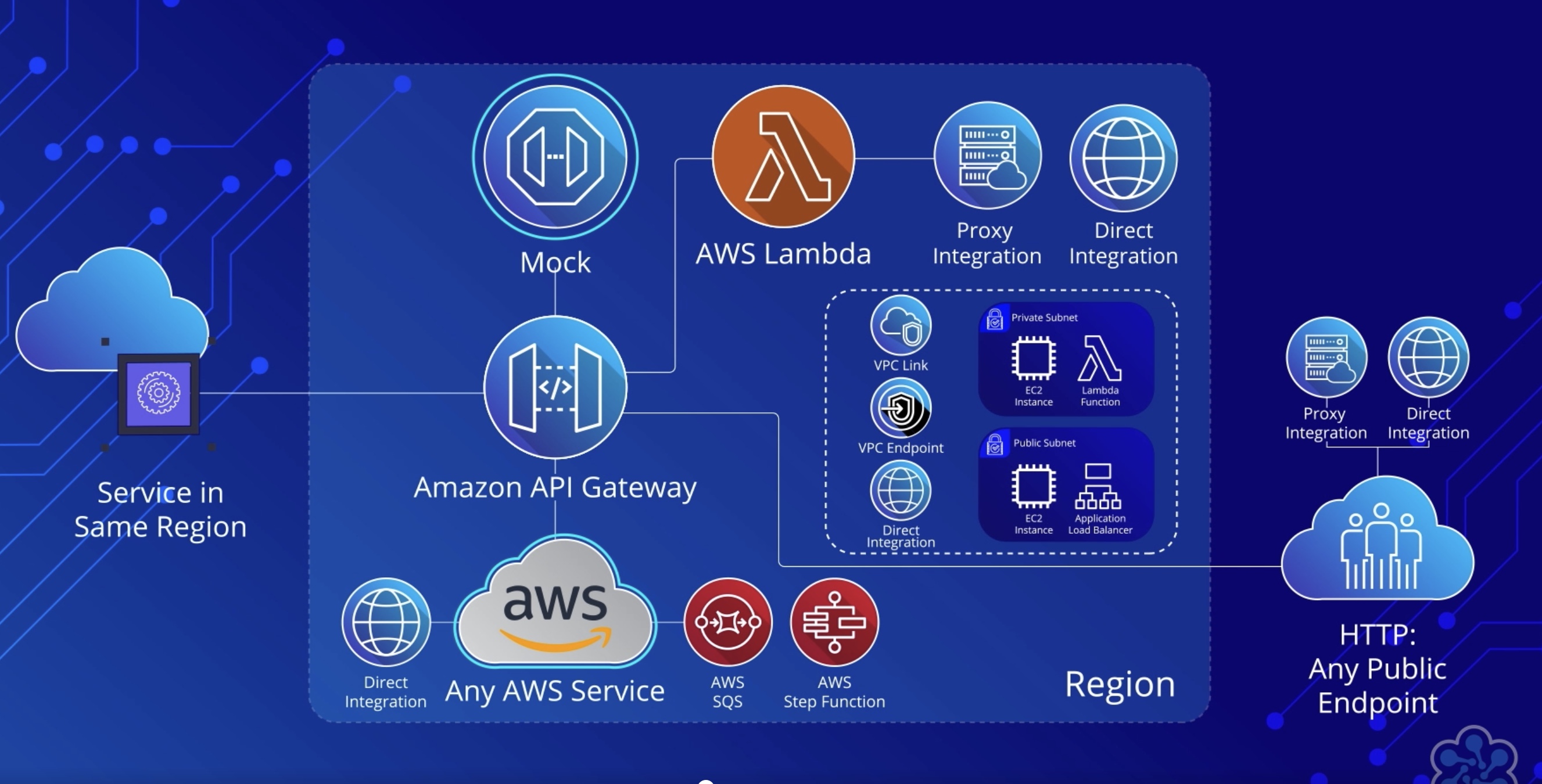
HTTP Endpoint 🛜¶
HTTP integration endpoints are useful for public web applications where you want clients to interact with the endpoint. This type of integration lets an API expose HTTP endpoints in the backend.
Lambda Fn ƛ¶
When you are using API Gateway as the gateway to a Lambda function, you’ll use the Lambda integration. This will result in requests being proxied to Lambda with request details available to your function handler in the event parameter, supporting a streamlined integration setup.
AWS Service 🚚¶
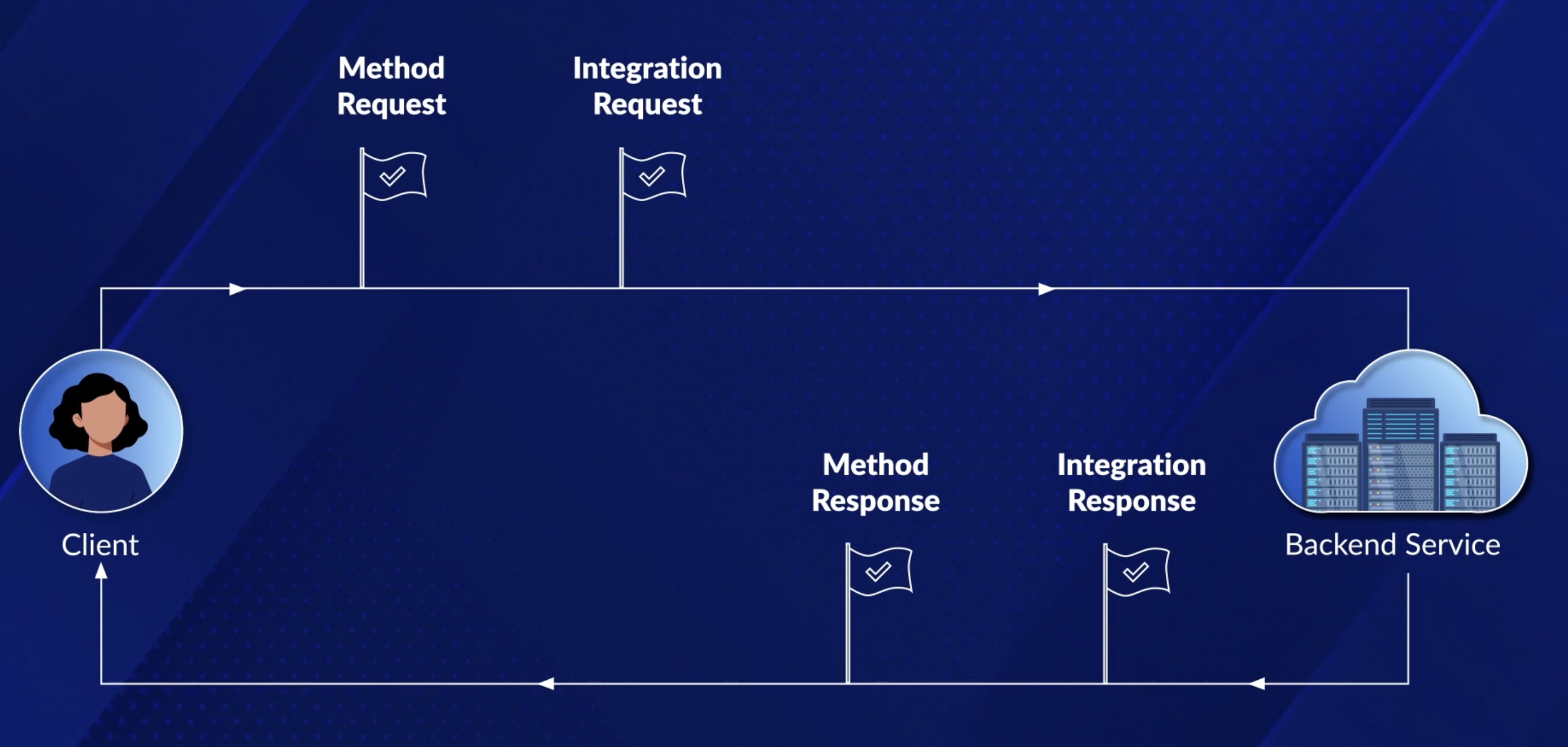
This type of integration lets an API expose AWS service actions. In AWS integration, you must configure both the integration request and integration response and set up necessary data mappings from the method request to the integration request, and from the integration response to the method response.
Example
You might drop a message directly into an Amazon SQS queue.
Mock 🃏¶
Mock lets API Gateway return a response without sending the request further to the backend. This is a good idea for a health check endpoint to test your API. Anytime you want a hardcoded response to your API call, use a Mock integration.
Request Response Lifecycle ♻️¶